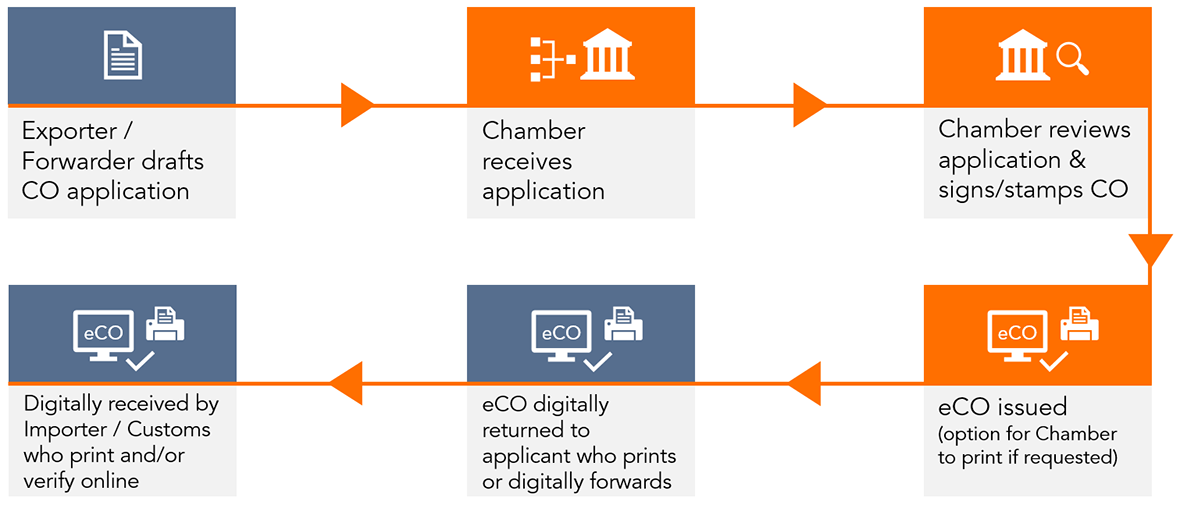
How it Works
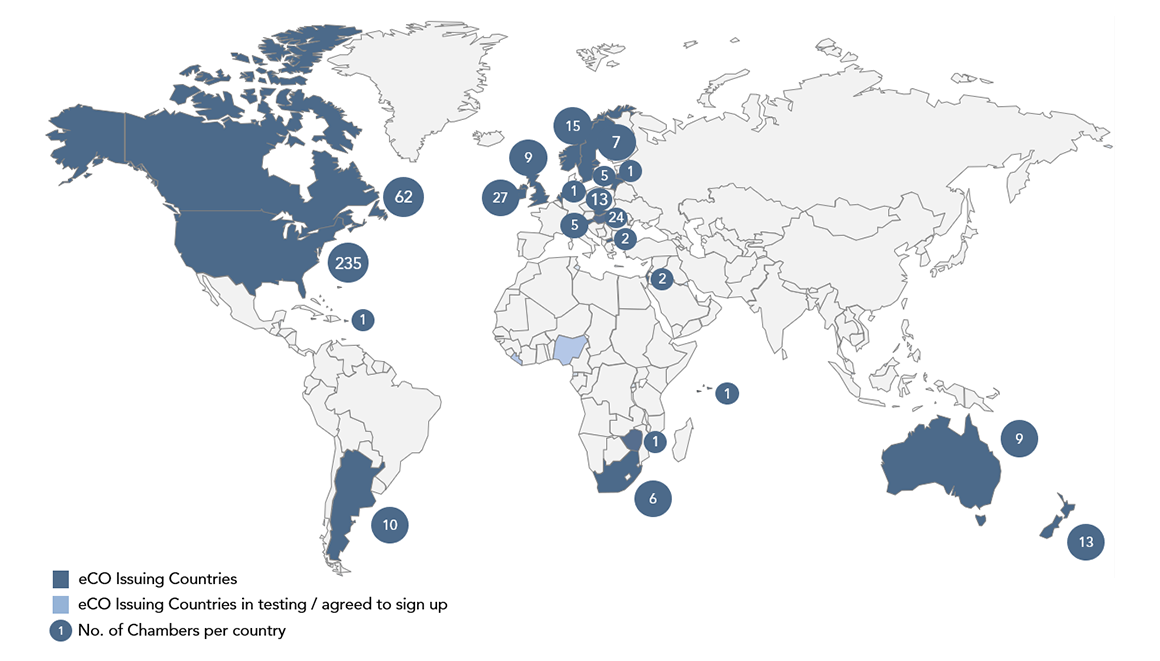
Where to eCertify
Exporters & Freight Forwarders can register at any of the essCert Chambers of Commerce or Certification Bodies here.
Exporters & Forwarders Apply & Submit
There are a number of ways for Exporters or Freight Forwarders to create and submit a Certificate of Origin application for certification:
- Web Submit: Draft CoO in essCert or upload PDF CoO and supporting docs as PDF & submit via essCert web-interface & collect back via Web App
- API Submit: Draft CoO in ERP, TMS, DocPrep, GTM solutions and submit with supporting PDFs via essCert API & collect back via API
- PDF Submit: Draft CoO in ERP or DocPrep solution, submit PDF CoO and supporting PDFs via email & collect back via email
Certifiers Manage Applications via the essCert Web Interface
Chambers of Commerce and other Certifying Bodies manage applications as follows:
- Payments managed by Credit Card, On Account or Invoice, option to interface to CRM & Billing systems
- Accept / reject applications via web-interface
- Single-Click stamp/certify or complete control over positioning, size, colour, font of signatures + stamps
Collecting Certified Docs
Exporters & Forwarders can collect certified documents by requesting:
- Digital Return, or
- Print+Post, or
- Print+Collect
Note: options available may vary depending on the Chamber of Commerce / Certifying Body, certificate type, and local regulations.
Printing or Forwarding
Applicants who use Digital Return will receive signed/stamped certified documents.
Verifying Certified Docs
Customs or Counterparties can verify essCert-certified docs as follows:
- essCert Verify: using the essCert Online Verification Tool
- ICC CO Verify: using the ICC's Online CO Verification Tool, provided that the issuing Chamber is part of the ICC CO Accreditation Chain
Adoption Timeline
Chambers of Commerce or other Certifying Bodies adopting essCert Express with a standard CO template can be setup and start testing within a few days.
Security
Key essCert Security Features include:
- Multi-tiered application environment, providing isolated tiers for web, application and data protected by dedicated firewalls and network isolation
- Enterprise wide risk management strategy at data centres including anti-virus, managed firewalls, secure access, network and host based intrusion detection
- Data encryption in transit and at rest
- Annual third-party security audits

